Internet of thing cloud digital technology design.IOT world security and data information.internet log in connecting.finger scanner. 6699629 Vector Art at Vecteezy

Uncovering Trickbot's use of IoT devices in command-and-control infrastructure | Microsoft Security Blog
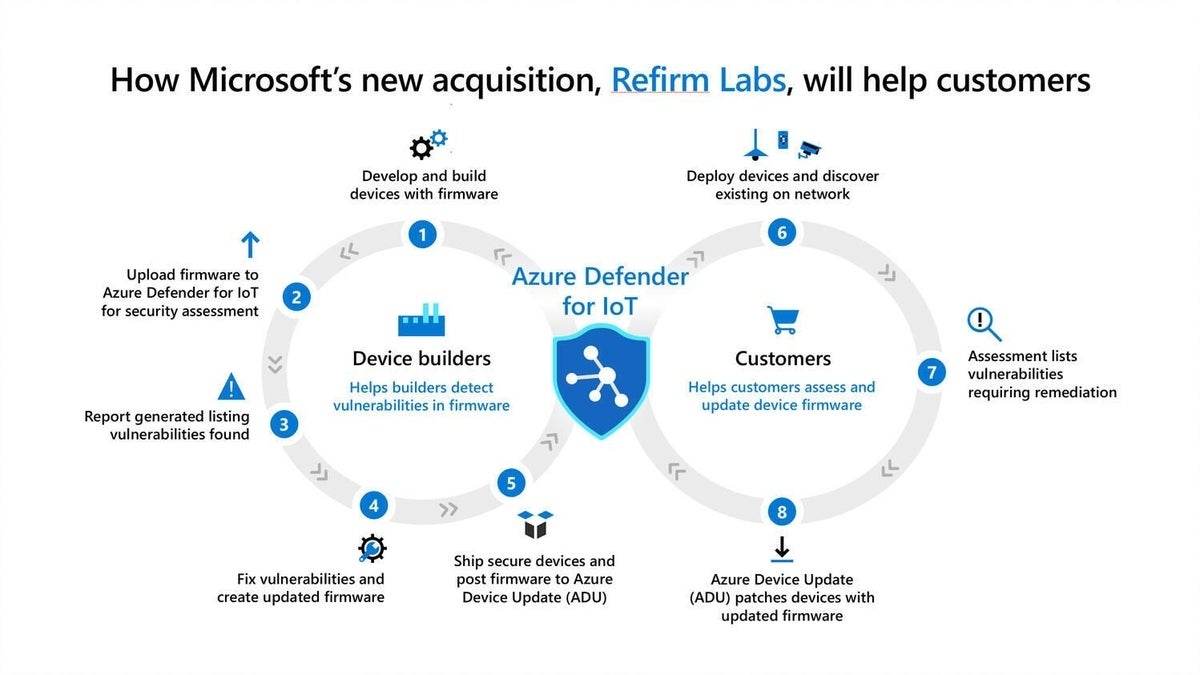
Microsoft's new security tool will discover firmware vulnerabilities, and more, in PCs and IoT devices | TechRepublic
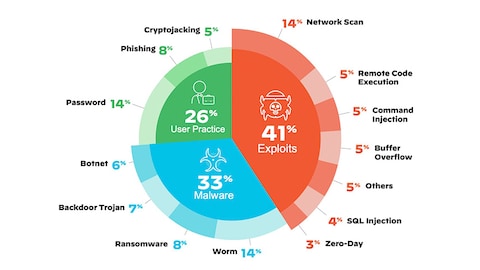
Sustainability | Free Full-Text | State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions

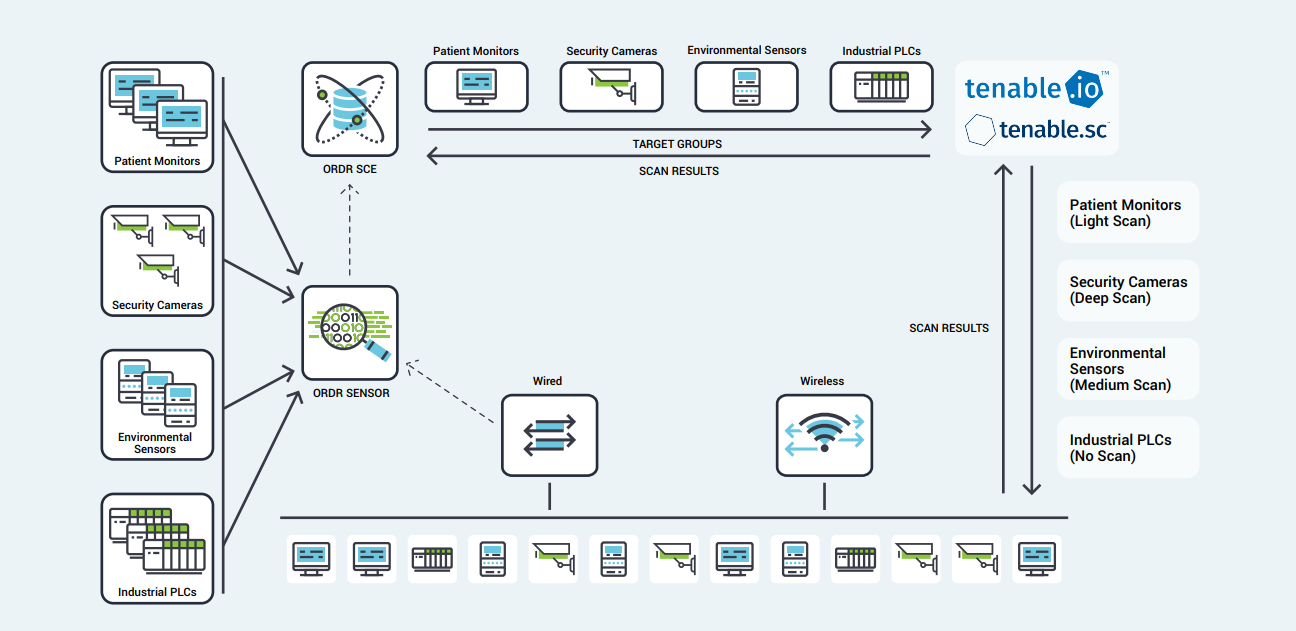
Intelligent IoT Vulnerability Scanner for communication service providers launched to assess and predict cybersecurity risks | IoT Now News & Reports

Check Point Software and Provision-ISR to provide on-device IoT security for video surveillance solutions – Intelligent CISO