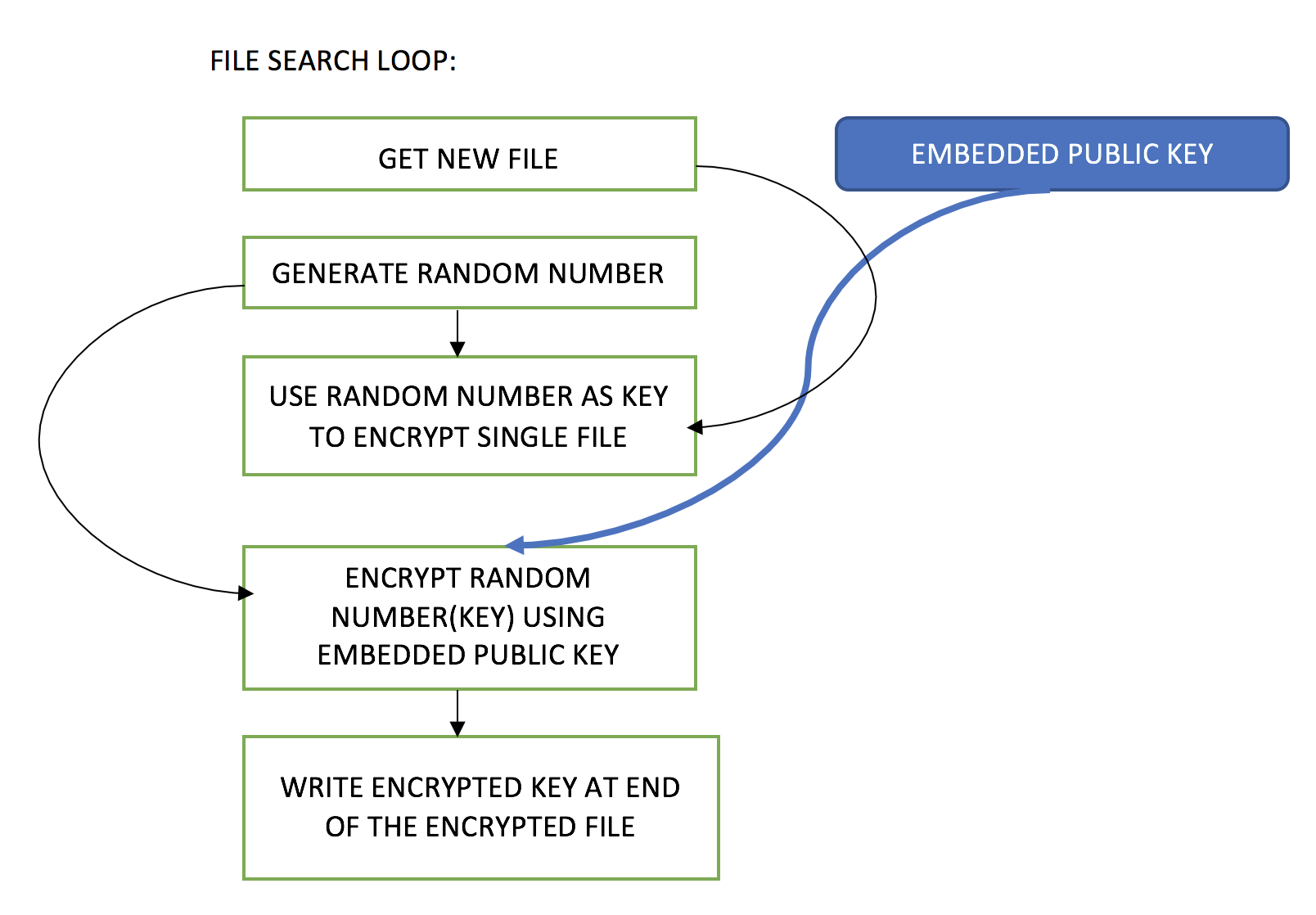
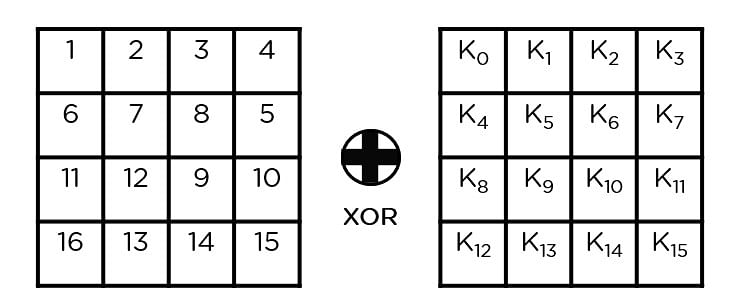
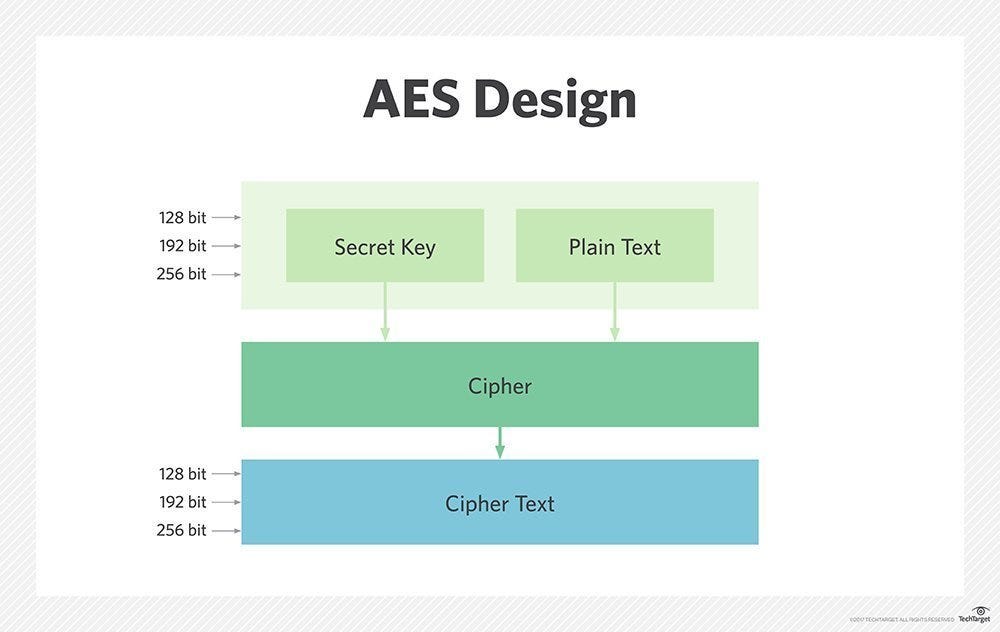
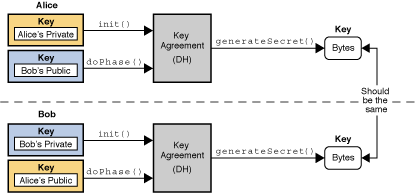
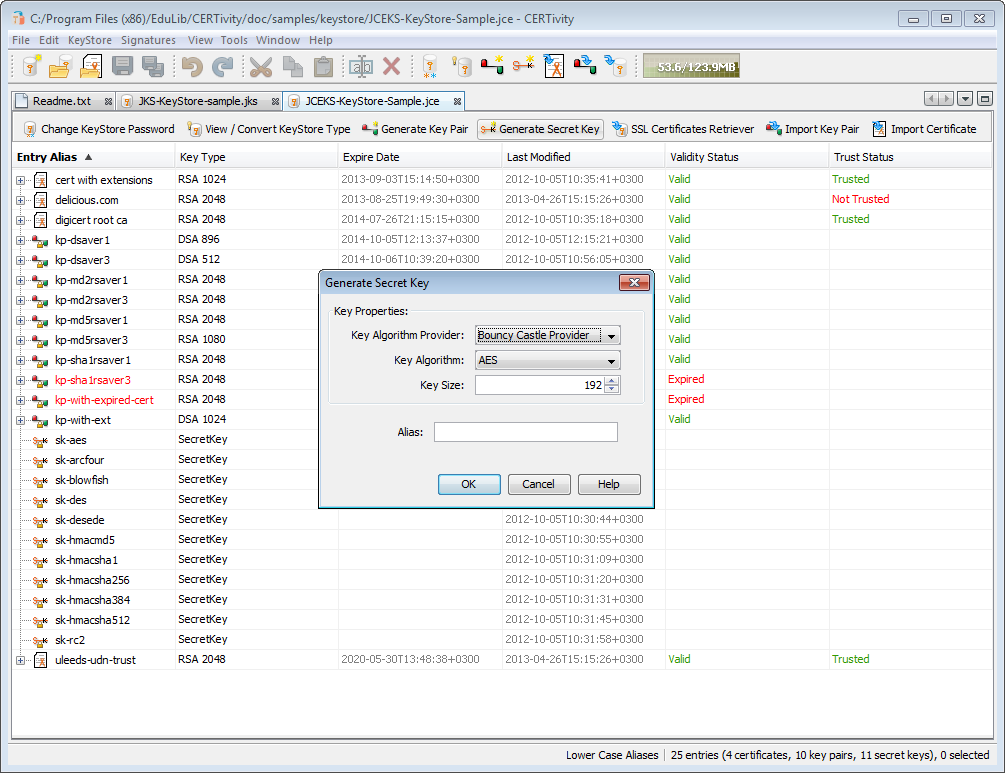
Key Generator and AES Demo Tool by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

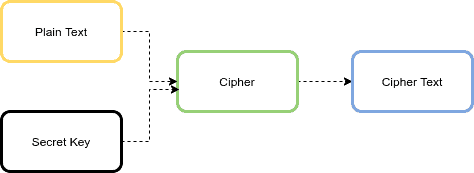
Encrypting and Decrypting a message using Symmetric Keys with Java, explained step-by-step with pictures | by Gregory Cernera | Medium

Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)

Symmetry | Free Full-Text | FPGA Implementation and Design of a Hybrid Chaos-AES Color Image Encryption Algorithm

Key Generator and AES Demo Tool by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

A one-round medical image encryption algorithm based on a combined chaotic key generator | Medical & Biological Engineering & Computing

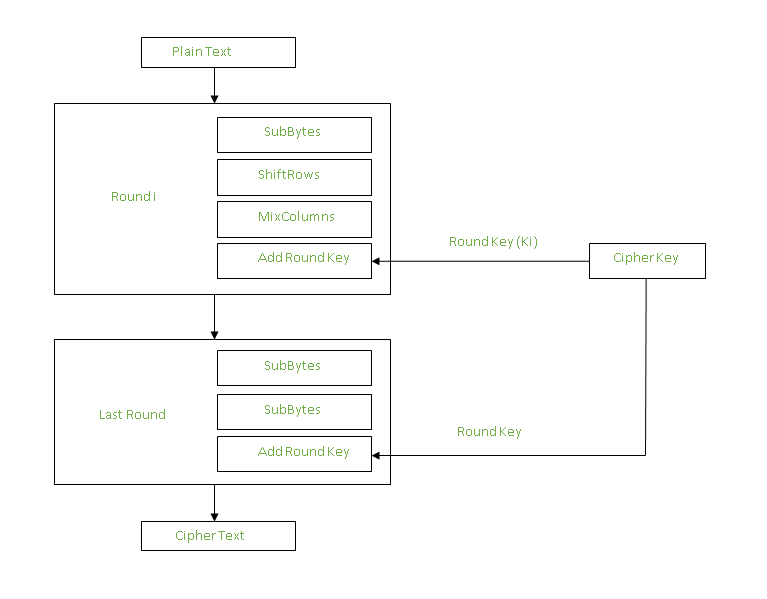
![MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-drmnd/ms-drmnd_files/image007.png)