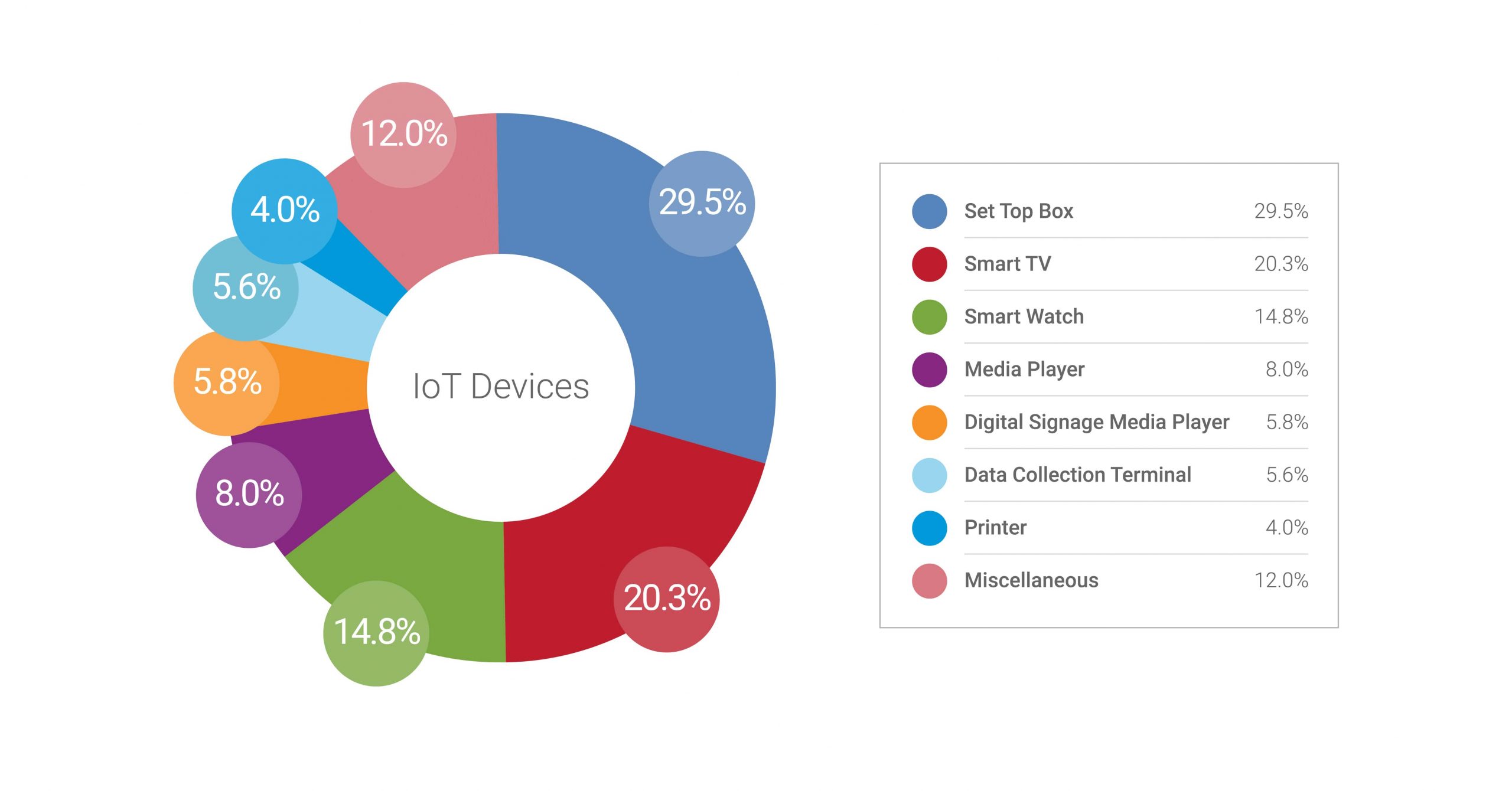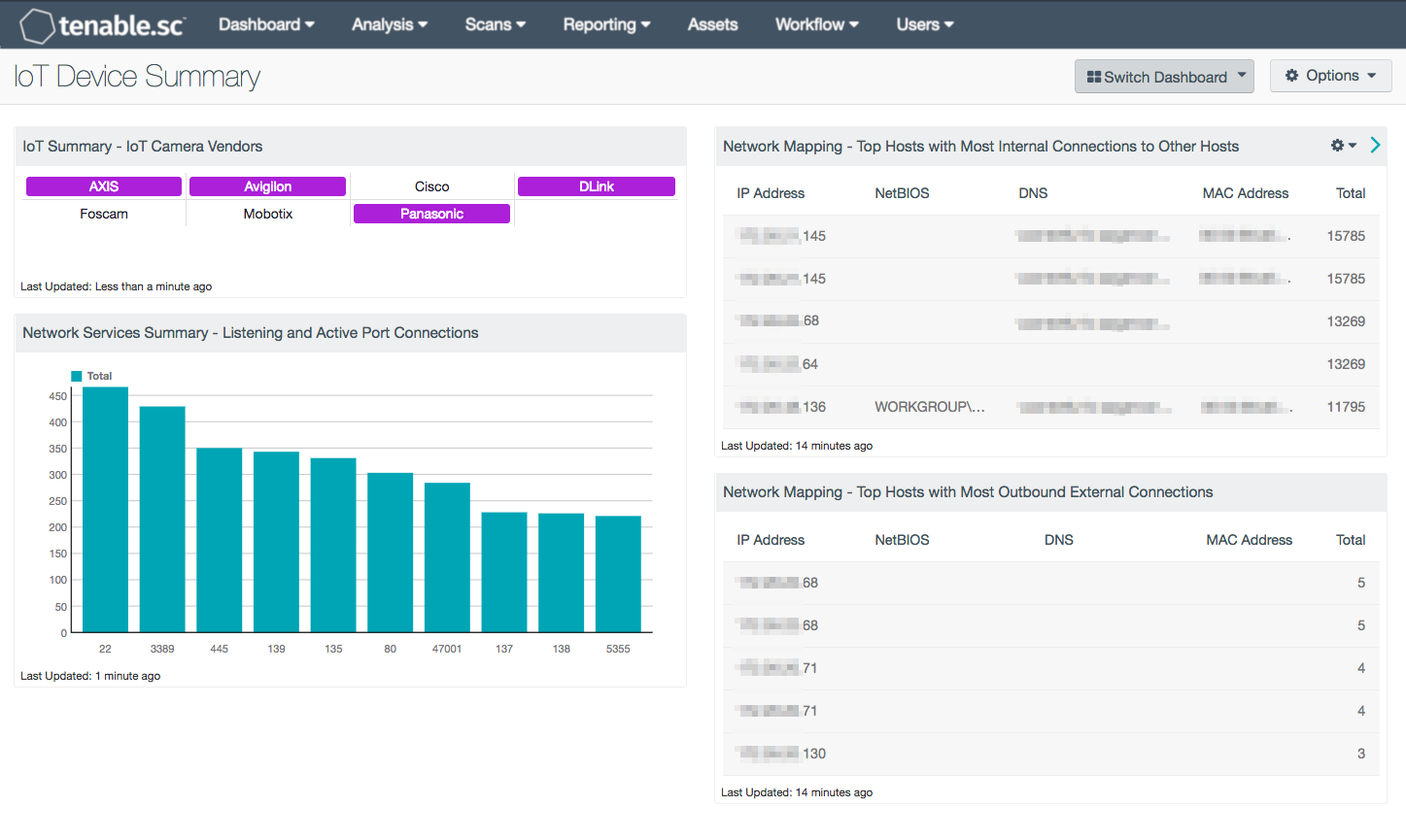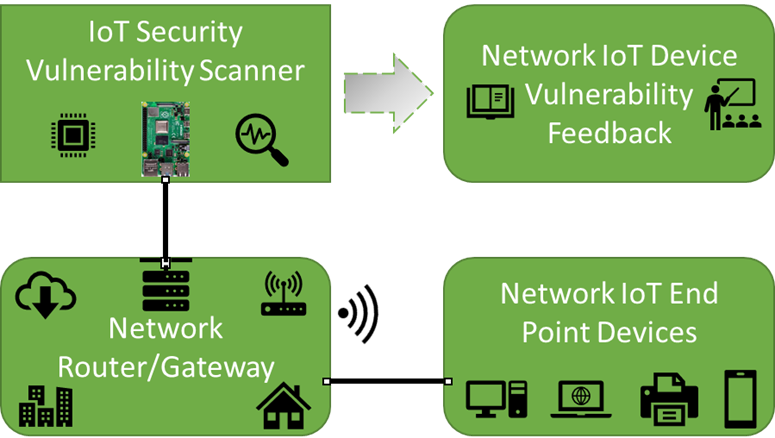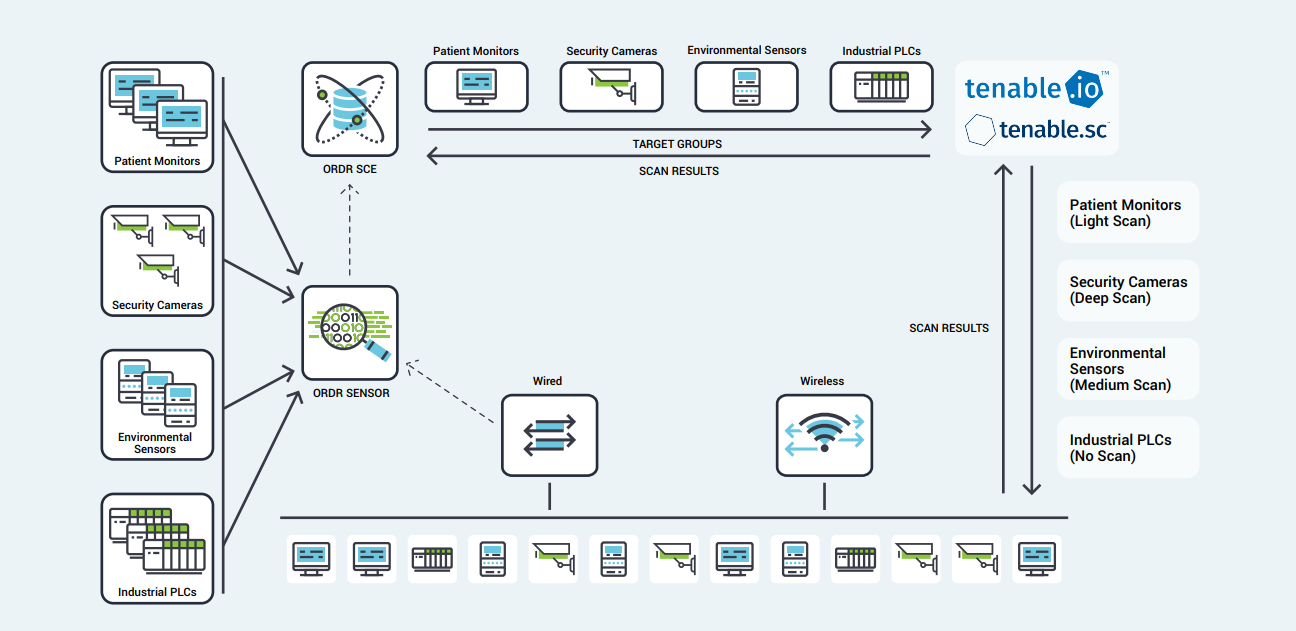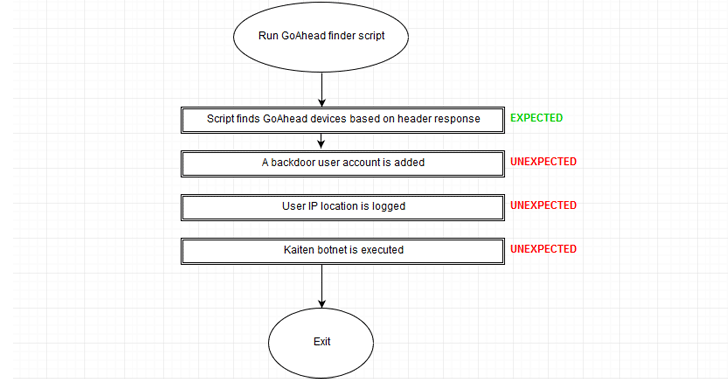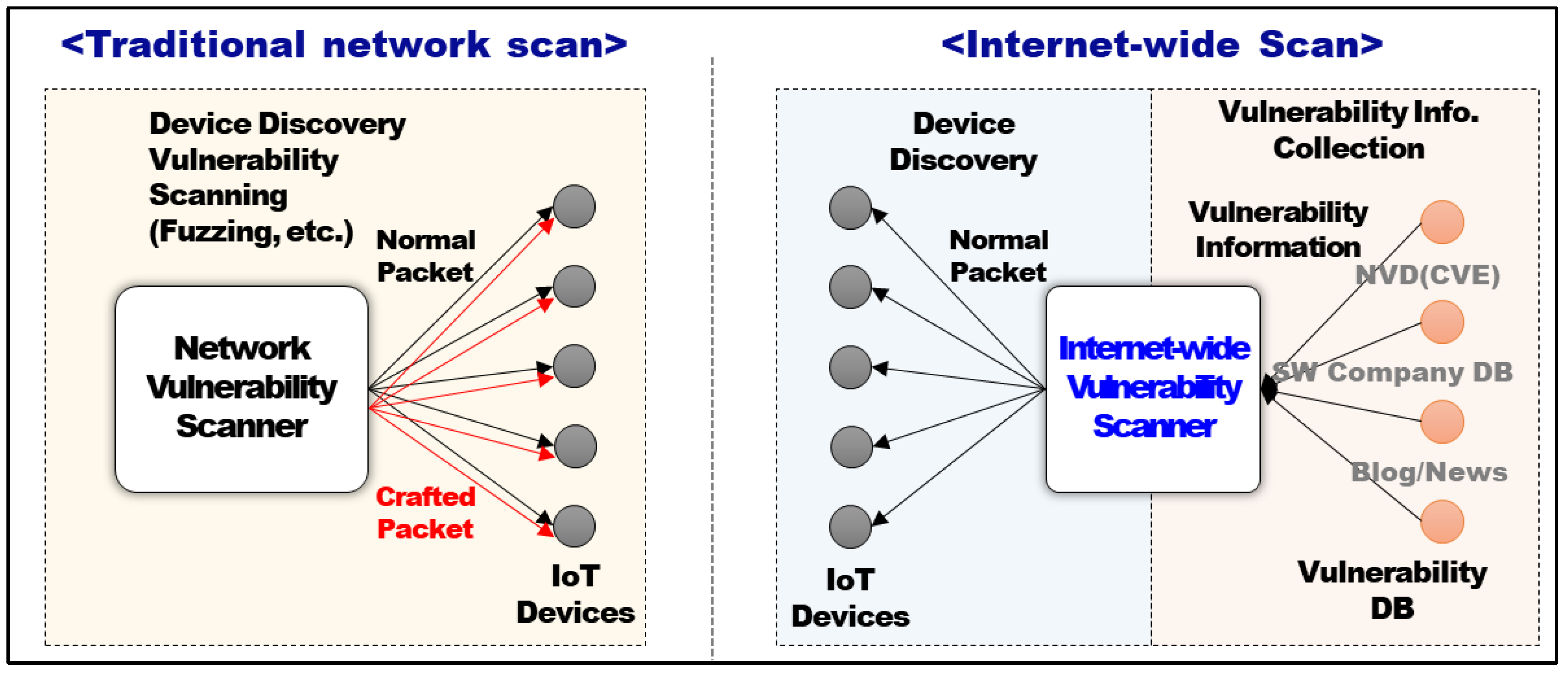
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices

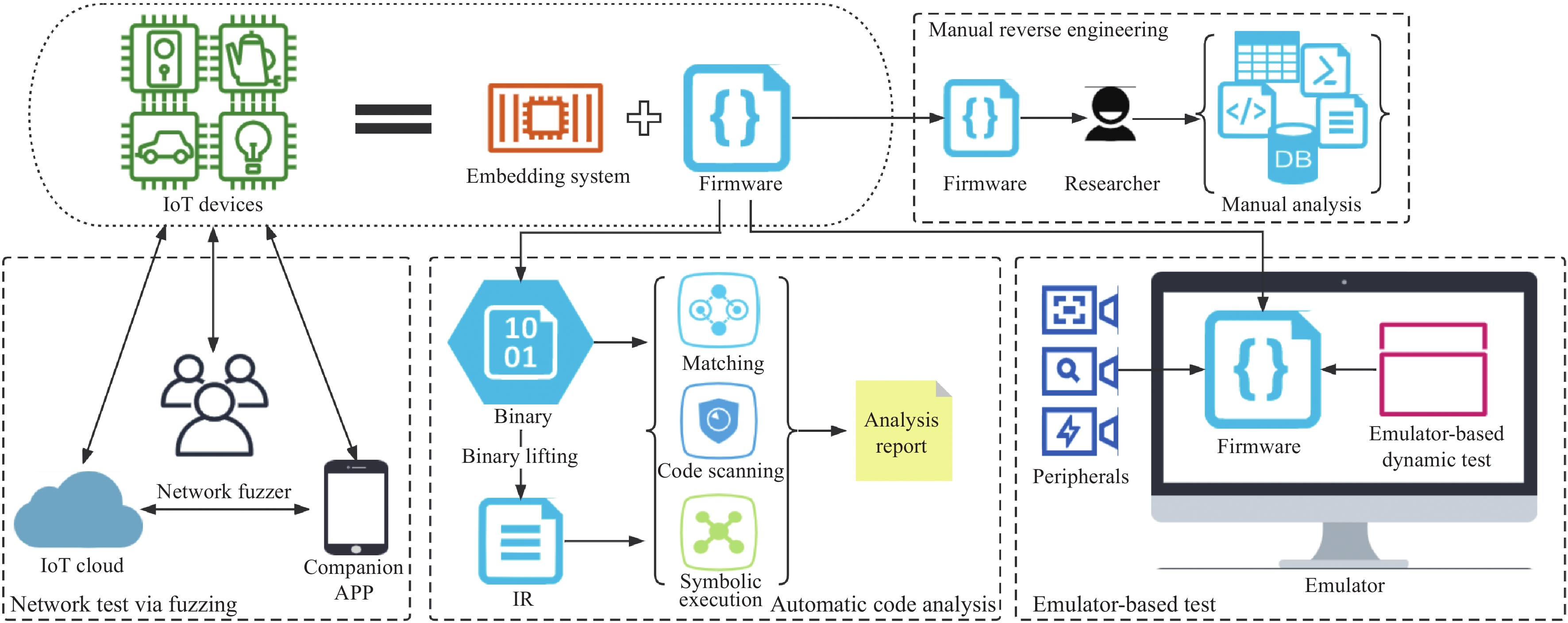
A survey on IoT & embedded device firmware security: architecture, extraction techniques, and vulnerability analysis frameworks | Discover Internet of Things
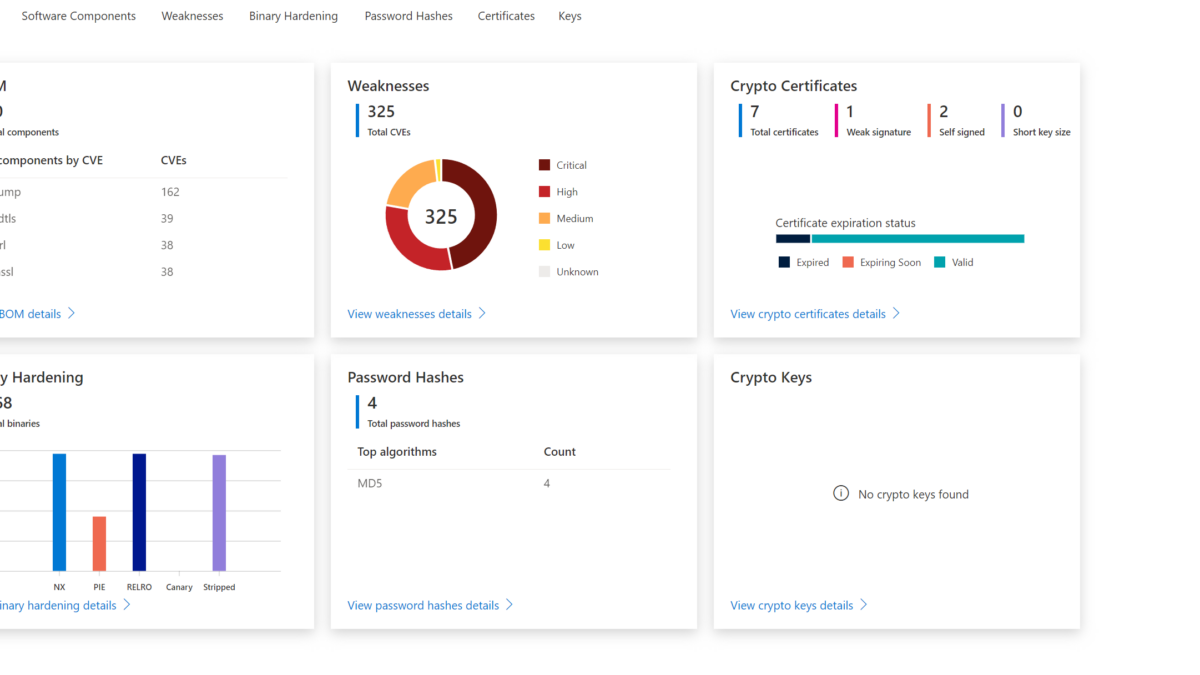
How to use Defender for IoT firmware Scanning for checking potential security vulnerabilities and weaknesses
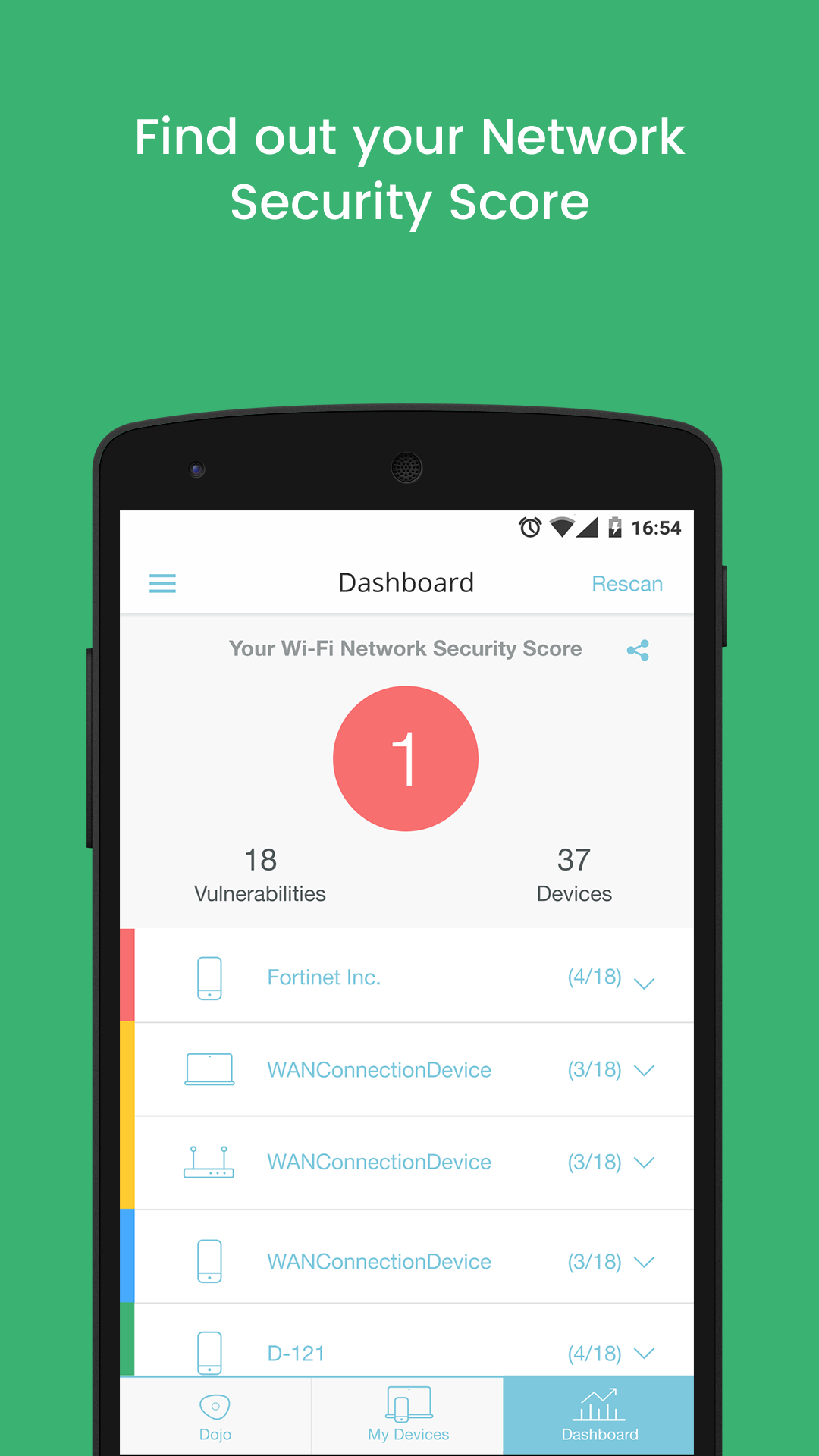
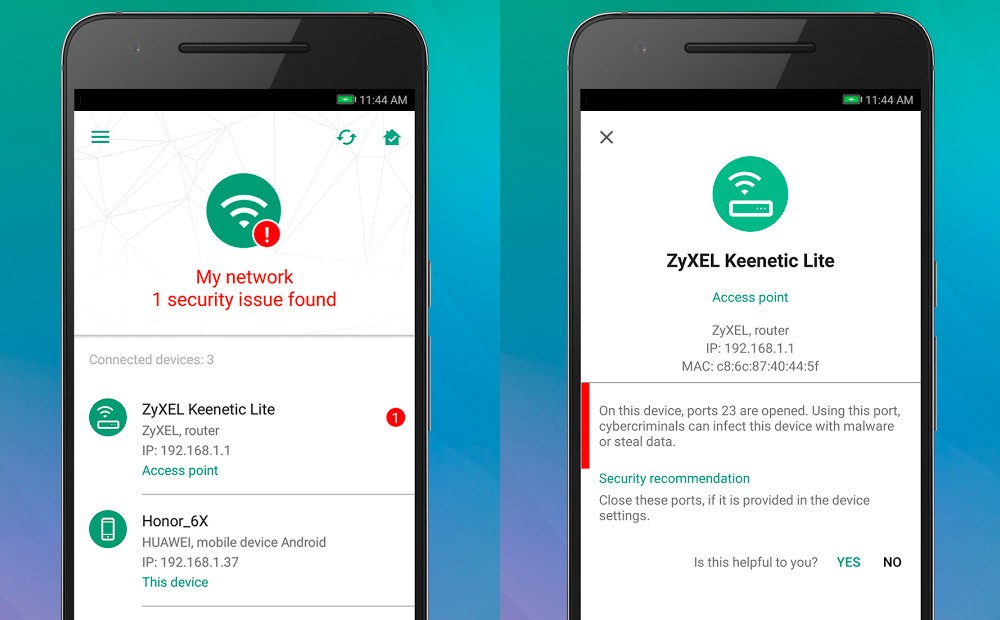
New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes

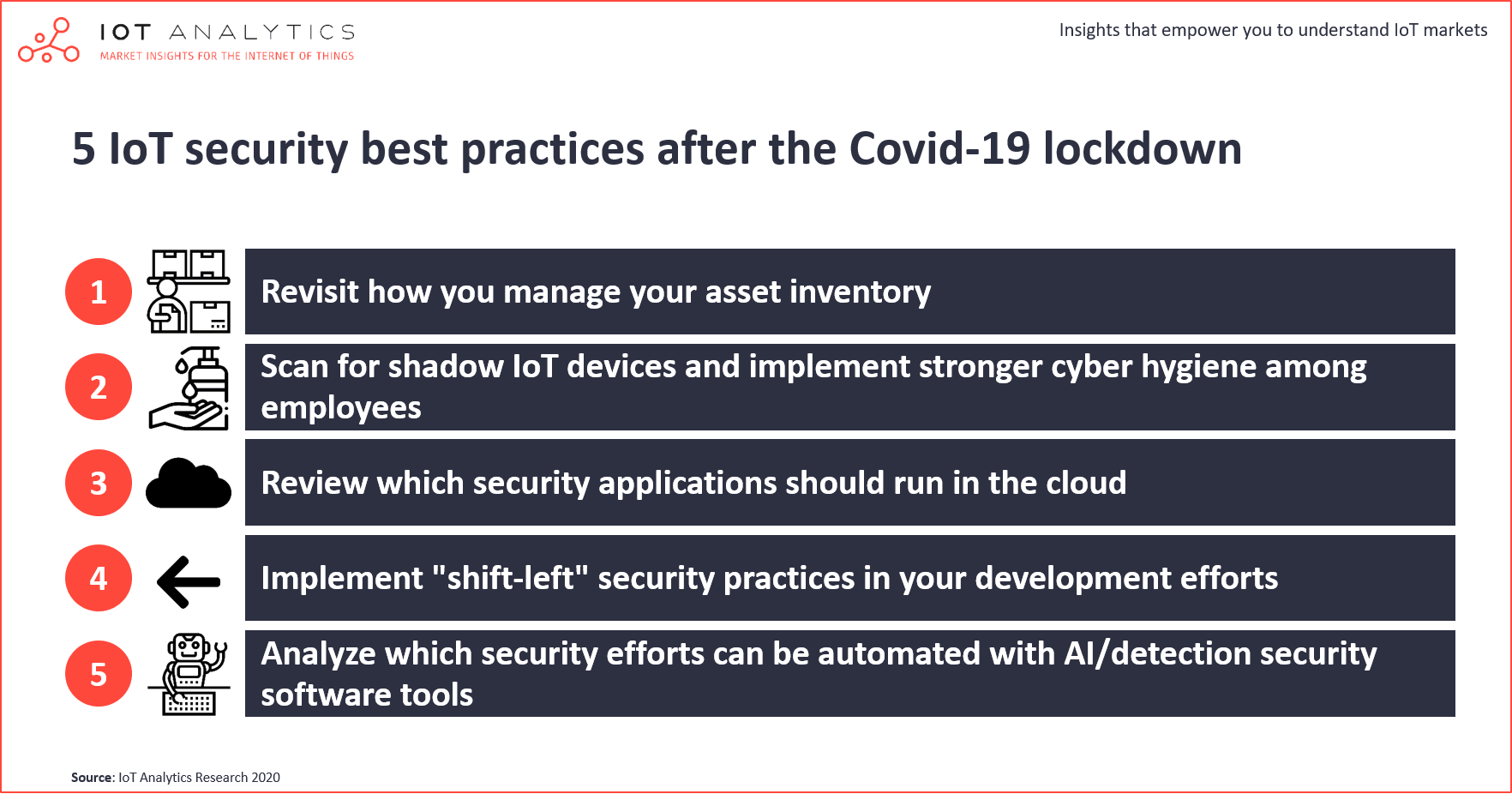
Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
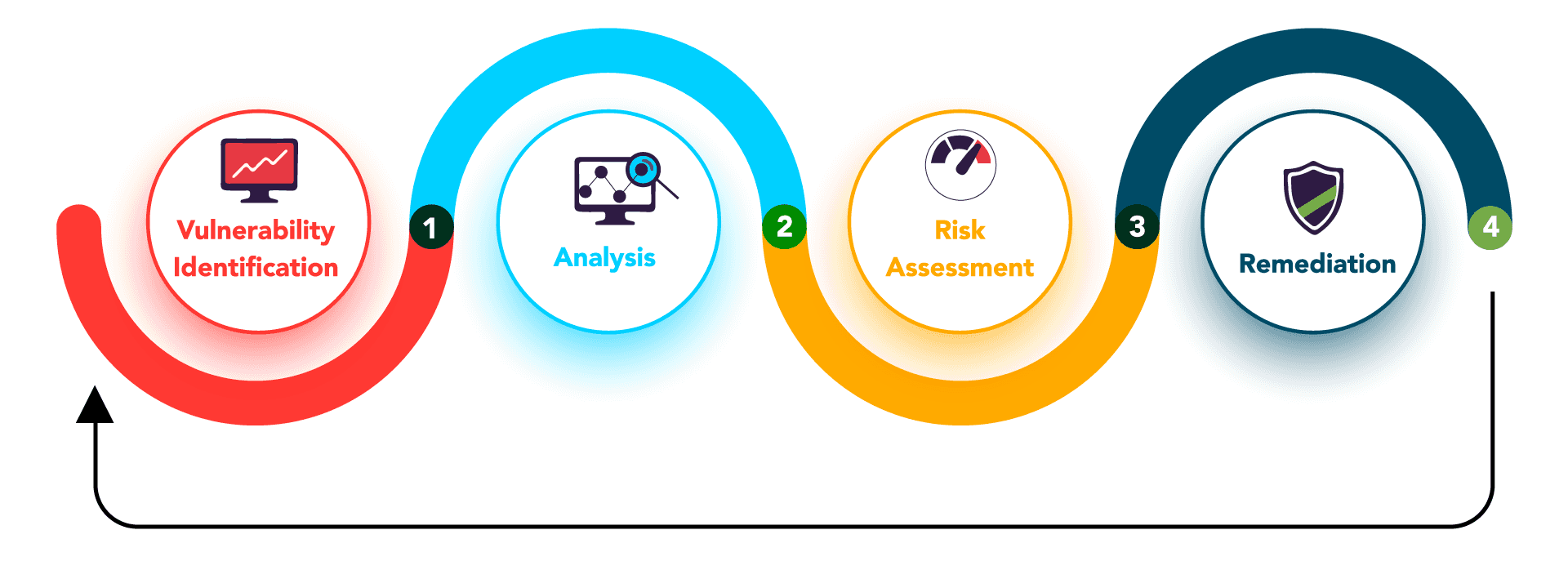
![PDF] The Forgotten I in IIoT: a vulnerability scanner for industrial internet of things | Semantic Scholar PDF] The Forgotten I in IIoT: a vulnerability scanner for industrial internet of things | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/135adee53b8f22156bba4bb774745e1ddc742357/2-Figure1-1.png)